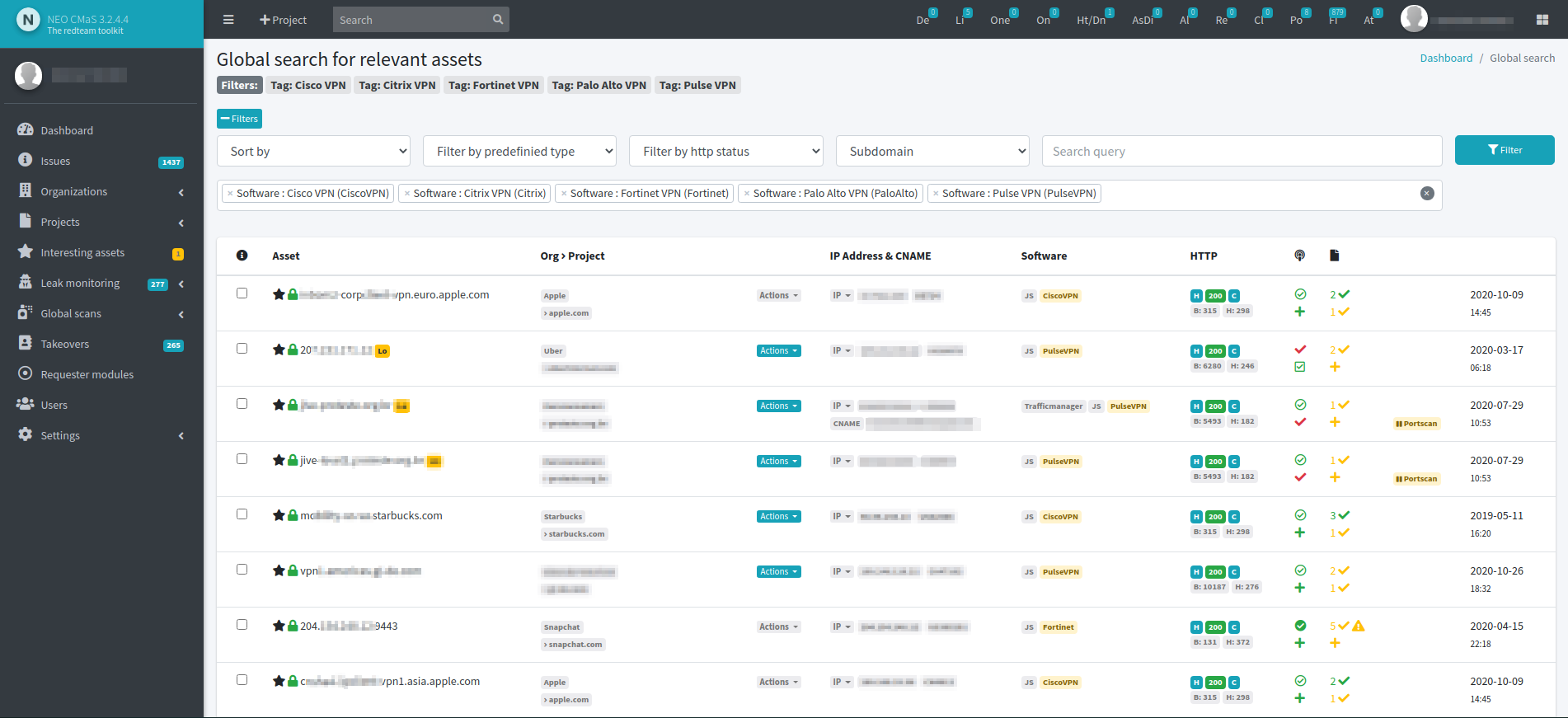
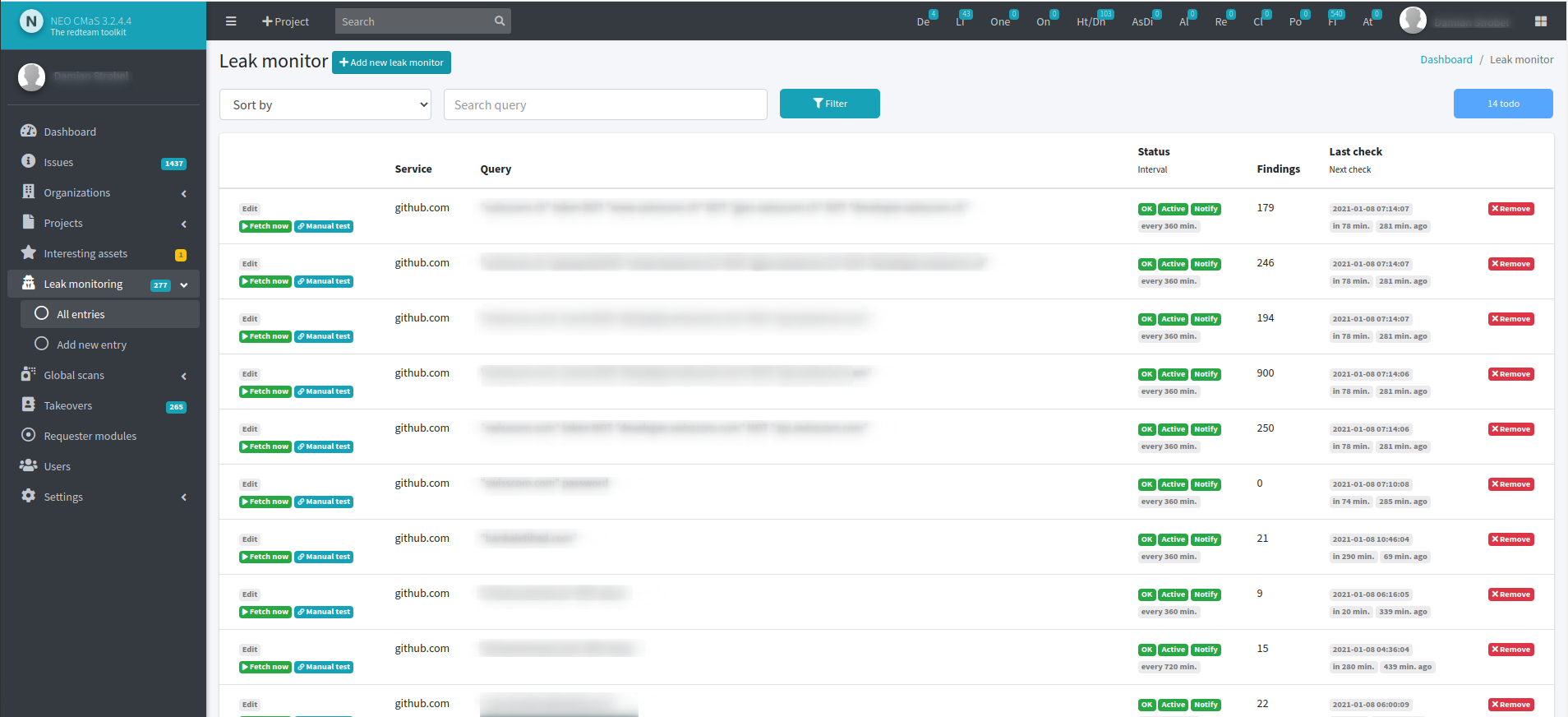
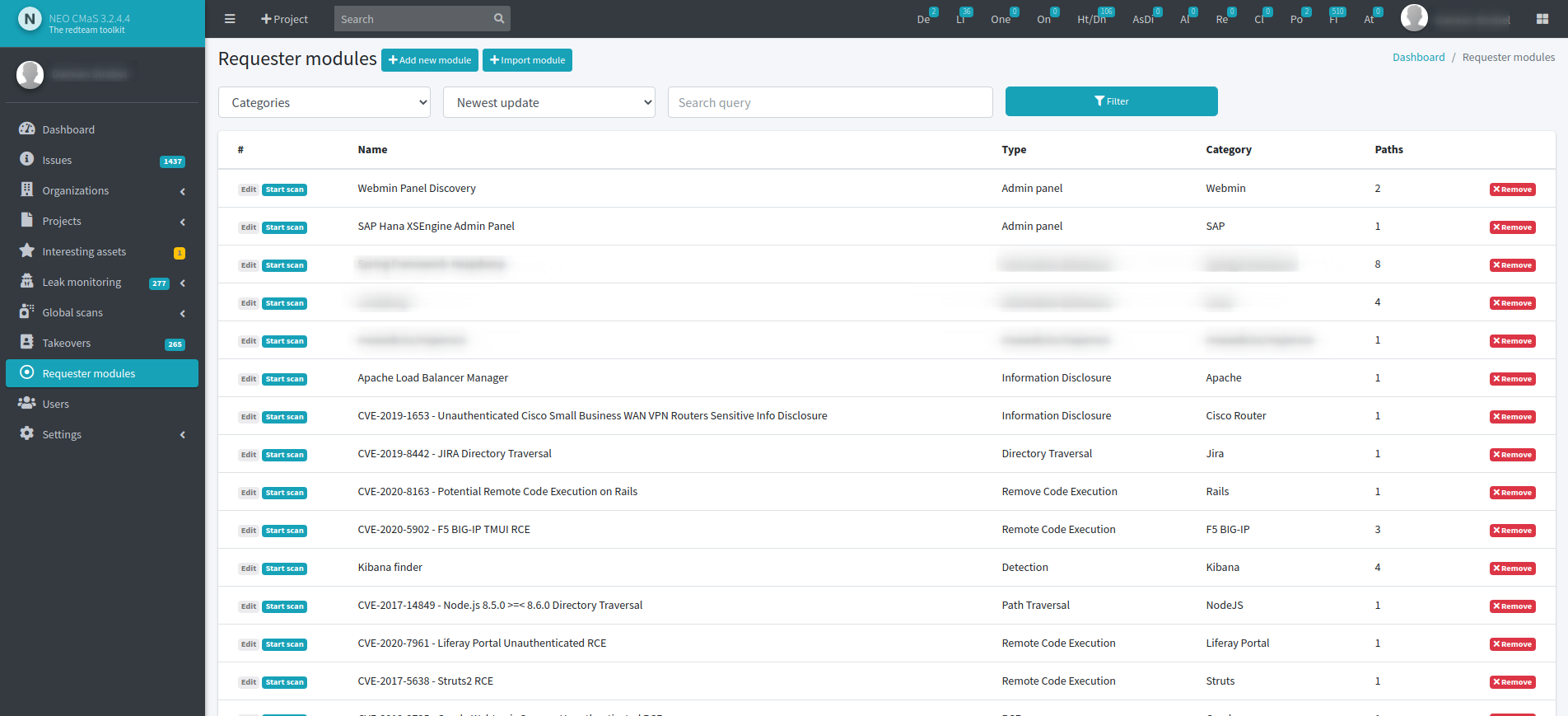
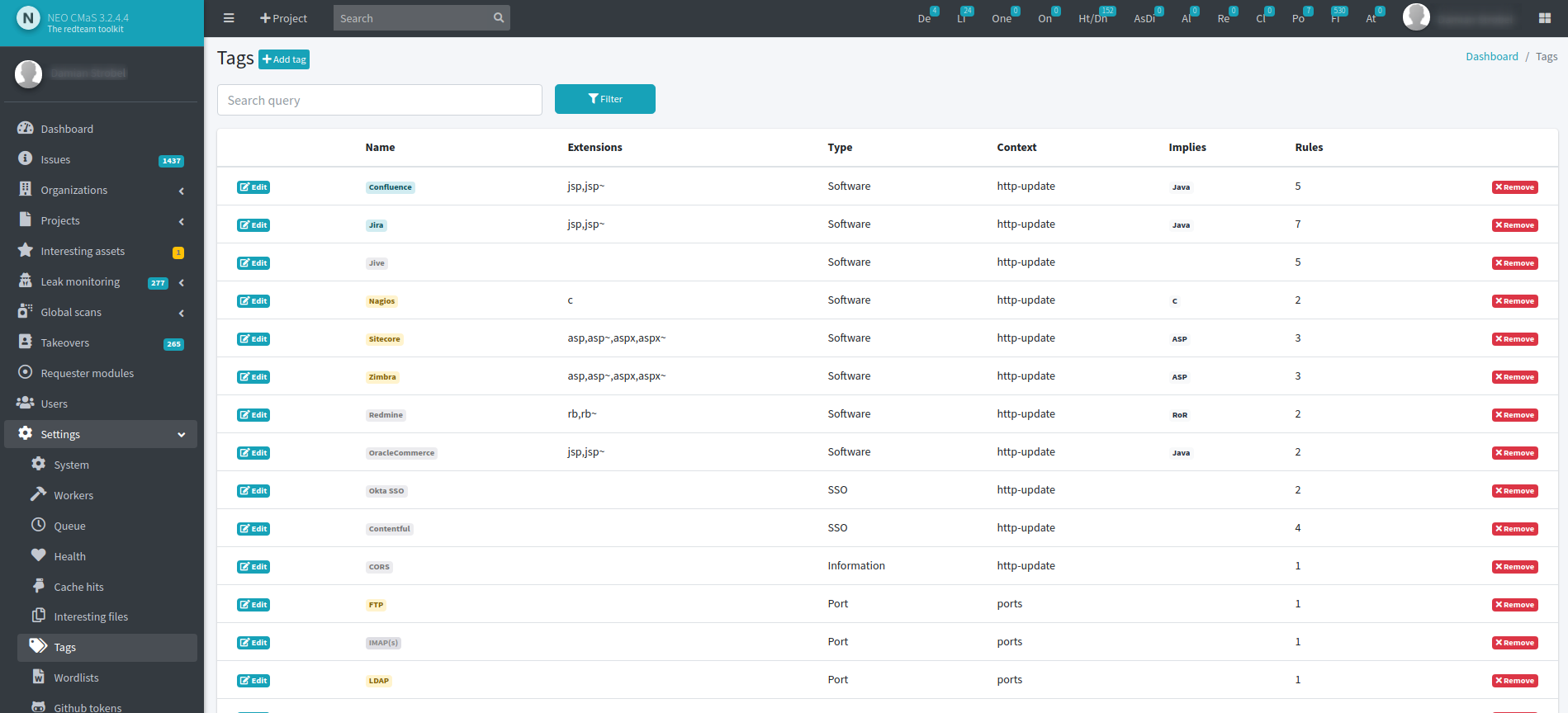
How much does NEO CMaS cost?
The price depends primarily on how many assets need to be checked and how often. The selection of the modules used also plays a role in the pricing, as do the additional services.
Can the system be bought on its own without analysts?
In principle, it is possible. However, your company should then be able to analyze and evaluate threats to IT security. Due to the large number of different IT systems and complex IT landscapes nowadays, a larger IT team is usually required. Small and medium-sized companies do not usually have the capacity for this.
Can NEO CMaS run on our internal network?
NEO CMaS is primarily a SaaS. Putting the software onto an internal network is theoretically possible, but currently only for governmental clients. In other cases, we use static IP addresses, as our IP addresses were whitelisted on this type of request in the past in order to allow NEO CMaS to see "more." A good middle ground.
How often is the system updated?
NEO CMaS is updated daily. It is the tool used during complex red teaming assignments. Everything we see and learn in penetration tests and bug bounty programs is entered into the system within hours. New ideas are implemented within a few days.
Can NEO CMaS also be used to secure Windows 10 PCs in offices?
No. NEO CMaS focuses on the external infrastructure (server, cloud, supply chain). There are better solutions for protecting work computers within a company, which we can also offer. The best thing to do is to send us an email with the specific request.
Can NEO CMaS replace penetration tests?
Even if software providers like to make such a promise, this is unfortunately not possible. No software in the world can match a person's creativity. A penetration test is usually very in-depth and is directed very selectively to a specific software/module/system. Human errors are often ignored in penetration tests. What good is the most secure software, if the complete backup has been on the Internet since the day before yesterday or if the access data for the company's VPN was leaked this morning? NEO CMaS allows an experienced team to see how they can best perform penetration tests. At the same time, NEO ensures basic security 24/7. A penetration test is usually over after a short period of time and may be repeated every few months.
Other questions?
If you have any further questions which have not been answered in the above, or if something is unclear, please do not hesitate to be get touch. We look forward to hearing from you.
NEO is a software which allows you to keep an eye on all your company’s assets. At a time when many companies are using “the cloud,” working with various agencies and freelancers simultaneously, mistakes can occur in an instant. Inexperienced developers can program vulnerabilities and data leaks onto a platform such as github.com or bitbucket.com, or simply make human errors – which can allow malicious attacks to penetrate your company and potentially steal your data. We read about such cases in the media every day: “the password was admin”; “The system was not updated because nobody knew it existed”; “A freelancer uploaded credentials to github.com.” These are all problems which we see on a daily basis and can lead to severe IT security issues. The functionality of NEO is based on actual hackers. No stupid CVE is scanned, and no warnings are sent out which are “false positives.”
Defining “Scope”
A true hacker knows how to attack, cause you damage, steal data, or leave your business paralyzed. You can make it easier for us by telling us your "targets.” Typical seeds in this case, refer to the domain of your company
(*.company.com); P-Addresses of address-ranges. However, the name of your company would be enough for us.
Defining exceptions
We don’t suggest defining exceptions, as this can lead to interesting attack scenarios. We can understand, however, that some companies may want a specific system, IP-address, or acquisition to be in “scope.”
An example could be a system, which runs under your subdomain (zendesk.company.com), but over which you have minimal to no technical control.
Short contracts and representatives
Everything will be recorded in writing as part of a short contract. In addition, a direct
representative from your company with technical expertise should be available in case we need to
consult with you or contact you about something critical.
Contractual questions can be clarified relatively quickly via email or through our contact-form. .
Maintaining basic data
One of our analysts enters the data you have provided (domain, IP address, ...) in the NEO CMaS. Next, NEO automatically tries to expand the "scope" (if allowed and appropriate). It looks at which hosts are used and searches referenced subdomains, while also looking for and providing data for dozens of paid APIs.
Data Enrichment
The system collects various types of data from your systems, such as HTTP-data, open ports, leaked employee passwords, etc. With the help of current and historical data, an attack surface is created for each of your assets and the system is able to carry out dynamic attacks for each system built.
Initial scans
Once all the relevant data is recognized by the system, it starts to create a variety of scans and tests. This includes searches for traditional holes in security (OWASP) as well as problems that we detect during a variety of penetration tests and red-teaming exercises. This also includes searching for forgotten files and leaked documents in addition to accessing data leaks from third party platforms such as GitHub. Every response we receive is then analyzed and evaluated by the system. Data that is of interest is automatically entered into the system and reused.
Bonus: our analysts
No robot, no bot, no scanner can completely replace a real human. But it can relieve a lot of the work! If you want to be on the safe side, you can book additional services. It is ideal if one of our analysts is responsible for your company. In addition to the automatic scans, manual scans are prepared, and your systems checked, manual tests carried out to find gaps that no software can solidly find (IDOR, ...) are crucial. We know from experience that there are situations where a trained employee simply has a "feeling", digs deeper and consequently finds critical gaps.
Reports
When NEO detects something amiss, an automatic notification is sent to one of our analysts, who reviews the information and determines whether the issue is irrelevant or of greater severity. More serious issues can, for example, refer to server configuration and/or leaks. It is therefore vital that they are examined manually! Anything serious is reported to you immediately. Communication is encrypted and sent via a channel of your choice within a few hours.
Continual repetition
IT systems are not static, and problems can occur at any time. Employees can mistakenly leak access data at any moment. NEO CMaS repeats processes to constantly hunt for new assets, scanning any changes. All options relating to this continuous scanning and all our modules are customizable. We can also scan monthly or hourly.
Step 1
starting point
All domains belonging to the company, including subdomains, are in the “scope” of the customer. The system has monitored around 300 subdomains over a long period of time - without any abnormalities.
Step 2
change
NEO CMaS updated all relevant data on the scope every 720 minutes. Various changes in the DNS settings of a subdomain were detected. These changes included typing errors.
Step 3
analysis
NEO CMaS has analyzed the new data and identified various anomalies and potential problems. A message was sent to an analyst so that they can take a closer look at the problem. There is a potential " subdomain takeover " via an incorrect CNAME entry.
Step 4
Security
The analyst notes that the CNAME has a domain that anyone can buy. Legacy Technologies GmbH bought this domain to ward off dangers.
Step 5
notification
The customer will be notified and can correct the error. Since this is a prestigious airline from the luxury sector, to which its own brand is particularly important, these types of "errors" are particularly critical . An attacker could use them for specific attacks (XSS, drive by download, ...) or use them to do black hat SEO. The latter would be bad for the brand.
Step 1
starting point
As part of a private Bug Bounty program on Intigriti, the scope of which only included a single subdomain (subdomain.company.com), it was more about a penetration test. The entire target system was behind a login. Nevertheless, we activated NEO CMaS for the goal.
Step 2
Scans
Since the system was isolated, automatic scans for typical security holes make little sense. An analyst made this decision. Only port scans and fuzzing for abnormalities and files were activated. Here, however, the intervals have been significantly shortened.
Step 3
Find
After a few days, NEO CMaS reported the existence of a file that had not previously existed. This was a backup file presumably created by an administrator or developer for a short time. NEO CMaS was able to discover and download the file. The significant thing in this case was the name of the file. NEO was able to create dynamic word lists for these types of tests. These are based, among other things, on the name of the company, the subdomain and the data the system sees. The backup file was named "subdomain.company.com.zip" .
Step 4
analysis
These types of discoveries can be anything and everything. In this case, the analyst was lucky. In front of him was the entire source code including the access data in the system's configuration files. In addition, this knowledge enabled him to carry out further attacks on the system, which led to the discovery of more than 5 different IDORs .
Step 5
notification
All finds were of course reported to the operator as part of the program and quickly closed.
Step 1
case study
The IT systems of an American hotel chain are continuously monitored by NEO CMaS. The infrastructure includes around 5000 different subdomains / IP addresses. Due to the size and the way in which the company works globally (freelancers, agencies, ...), significant mistakes happen again and again - these are avoidable - in theory. In practice, you need someone who makes sure that everything is really in order.
Step 2
scans
In this phase NEO CMaS runs on standard settings - these are very suitable for many companies. After a few months, the system was able to find a faulty server configuration on an old subdomain: the contents of folders were output. In many cases this is not a problem, in this case it was because one of the folders NEO checks is "uploads /".
Step 3
find
NEO was able to find a large number (around 10,000 PDF files) in the "uploads" folder. The findings have been reported to an analyst so that he/she can assess whether this is a case that needs to be reported.
Step 4
analysis
The analyst recognized within seconds that this folder contained tens of thousands of hotel chain invoices. Since this is so-called PII data, this can quickly end badly - especially for a US company. In the past, fines for these types of "problems" ran into the millions.
Step 5
Incident Response
A case like this usually leads to a deeper investigation, in which one has to see whether the attack already stolen data and how one has to react to it. Usually, the PR department is involved by the board quickly - you don't want to lose face completely.
Step 1
notification
The client is a large corporation with hundreds of subcontractors and its own CIDR, which includes around 128,000 IP addresses. The scope here is "the company" and everything that goes with it. The company has its own red team but cannot keep up with the work. Only a few dozen of 100 positions can be filled. Automation is all the more important.
Step 2
use case
The collaboration began around the time the famous Citrix VPN exploit was published. The question was whether NEO CMaS could find more of these vulnerable systems within the infrastructure. IT was certain that it had found and updated everyone. Due to the size of the network and the internationalization, there was little doubt.
Step 3
data preparation
NEO CMaS was able to automatically find almost all assets belonging to the company. The "golden residue" was found by one of our analysts with the help of special techniques (permutations, alterations, fuzzing) within various wildcard domains. The deciding factor!
Step 4
finds
In addition to various other security gaps, data leaks inside and outside the company's IT systems, 7 other Citrix servers were found to be vulnerable. A result that surprised even corporate IT and a good argument for continuous asset monitoring.
Step 5
Incident response
The client was especially shocked by the existence of the AWS access data. A deeper analysis of the data and, above all, the rights of this access data showed that an attacker had access to the entire cloud infrastructure of the company on Amazon. These cases cannot be more critical.
Step 1
starting point
In this case we had a small infrastructure with around 10 different IP addresses and a good IT team that had their own servers under control. As part of a proof of concept, NEO could not find anything. Nevertheless, the collaboration was able to continue - because timing often matters when it comes to weak points. The customer was also aware of this.
Step 2
Scans
Here too, the standard NEO settings were used. NEO does not only have known methods and vulnerability scans but also work with previously unknown vulnerabilities and techniques. Often these are exactly the methods that lead to success.
Step 3
Finds
One of these techniques was able to automatically bypass the server-side protection, which previously ensured that so-called "heap dumps" of Java software were only available to the internal team. The bypass allowed everyone to reach all Spring Actuator endpoints.
Step 4
analysis
Heap dumps are complex files that can be anything and nothing. Sometimes you have a heap dump, which doesn't contain any interesting data. This was not the case. The heap dump contained dozens of access data to various systems. The icing on the cake would be hard-coded Amazon AWS credentials.
Step 5
Incident response
The client was especially shocked by the existence of the AWS access data. A deeper analysis of the data and, above all, the rights of this access data showed that an attacker had access to the entire cloud infrastructure of the company on Amazon. These cases cannot be more critical.
Step 1
starting point
This company has around 35 different subdomains, works a lot in the AWS Cloud - a small but interesting infrastructure. With NEO we also try to look outside - attacks happen in a wide variety of ways; for example, an employee being hacked or somehow losing data.
Step 2
Scans
NEO CMaS has been monitoring the company for months - with no results. There are no security holes, no old systems, no misconfigurations. Everything looks good. What NEO also does is monitor external data sources - this is where github.com plays an important role.
Step 3
finds
After the leak monitoring module was activated, NEO was able to find 4 different leaks in the next few weeks. This is always about the leak of access data to various systems of the company. An attacker is particularly fond of this. Access data to Github itself and the company's Artifactor Server were leaked twice. This gave the attacker access to private software which could in fact, then be changed.
Step 4
analysis
With this type of discovery, it is imperative to always check whether the data is valid and usable. You often see that access data as been leaked, but it can only be used if you have access to a certain server or if you are in the internal network. Regardless, these occurrences are reported to the company, because it is precisely these small pieces of the puzzle, which create bad image in an emergency.
Step 1
starting point
In this case, everything happened in the context of the "Bug Bounty Program". The company is a US telecommunications provider with hundreds of thousands of assets and IP addresses. A big target – the type of thing NEO CMaS was made for. In the current case, it is relevant that, with the help of a chargeable API, NEO was able to automatically include a new asset into the monitoring. It became apparent that this was vulnerable.
Step 2
Scans
Due to the amount of assets, we used settings that resulted in less than 1000 accesses per asset (per run). We therefore found a good balance between speed and result. Dozens of problems had been reported to the company itself. The one described here is particularly interesting. The open port 81 on the IP of the asset was found and scanned. NEO CMaS examined all files it saw.
Step 3
finds
Fuzzing found a Javascript file that contained a particularly suspicious signature. In addition, a "download.asp" was found in one of the directories. The response from this file was an HTTP status 200 with no content - something such as this, is always considered “interesting”.
Step 4
analysis
In the Javascript file, our analyst was able to see the structure of requests to another file, therefore building an access with the help of Burp Suite, which would be accepted. The result was the ability to write files with their own content and file extension to any folder on the underlying Windows server. This is effectively the famous "Remote Code Execution", in which you put a shell in the www root. The discovery was named a "critical find."
The best protection: be better and faster than the attacker – thanks to NEO
- 24/7 continual monitoring and scanning of your assets.
- NEO automatically searches for new assets belonging to your company in short intervals – you just have to input a “seed” into NEO.
- Shadow IT is a big problem – NEO’s alteration engine is able to reliably find these kind of assets and monitor them regularly.
- NEO not only scans for known security vulnerabilities but uses targeted fuzzing to find anomalies. Our analysts often discover that these anomalies are serious gaps in security. Thanks to our extensive fuzzing modules, NEO was able to find “0days” in globally used software such as Github Enterprise
- Machine learning methods are used to optimize settings for automated attacks and checks – the aim is to create the greatest possible coverage within a small number of accesses, making NEO useful against live/production environments.
- In addition to traditional security issues, NEO also searches for data leaks, incorrect configurations, or leaks on external portals. A real attacker often takes the easiest route.
- New risks can be created from the widespread use of Cloud providers. NEO proactively defuses any issues by automatically taking control of referenced subdomains, for example, and withdraws access from attackers.
- NEO is scalable and therefore able to scan millions of assets several times a day when necessary. This is how we guarantee continuous monitoring – a real attacker works in the same way—waiting for someone to make a mistake.
- NEO prepares large amounts of data – port scans, file scans, etc. – making sure that trained red team members can extract relevant information at a glance. Not everything can be automated!
- Requester modules allow you to install your own modules to scan for company specific problems in a convenient frontend.
- NEO is battle tested. Our analysts successfully use the program daily against heavily protected assets such as PayPal, AT&T, and Daimler. Furthermore, NEO CMaS has proven itself in complex environments (KRITIS) and is an official part of “RAFAEL Cyber Defense Center – RDCD” – the product of Israeli company “Rafael Advanced Defense Systems Ltd.”
- Knowledge of new IT problems is put back into our software for continuous improvement. NEO is a system which is constantly being optimized by real hackers.
Would you like proof of concept?
Because we are confident of NEO’s capabilities, we offer interested parties a short trial period to try out the tool. You will receive a brief report on what was found in a short time period and potential initial attack-vectors. One of our analysts will sit with you and discuss the report to give you valuable tips. Of course, this is only a snapshot – if IT security is really important to you, you can have your own infrastructure monitored non-stop. It is well known that mistakes occur regularly.
Request POC/Demo